Agent Verification: A low cost and simple approach to battle Social Engineering!
- Midships

- May 21, 2024
- 5 min read
Updated: Sep 19, 2025

Executive Summary
This paper outlines Midships’ approach to combat social engineering fraud, focusing on the scenario of phone call-based attacks. The solution presented in this paper enables agent verification via Time-based One-Time Password (TOTP) technology that can prevent malicious actors from successfully impersonating call center staff. The solution allows customers to authenticate an agent from the organization using their mobile devices, even in offline mode. Midships can provide expertise and capabilities to organisations, integrating this solution into their existing infrastructures to better protect their customers.
Background & Purpose
Frauds involving social engineering are a significant security concern for organisations as they directly target the human element, often the weakest link in the security chain. Finding a solution to mitigate the risk of customers becoming victims of fraud from social engineering can be extremely challenging, as this problem revolves around human nature and psychology. In this paper, we focus on social engineering through phone calls. Compare to other mediums of communication, phone calls allow the malicious actor to exert pressure and practise psychological techniques such as cold reading and neuro-linguistic programming. Therefore, phone call-based social engineering has a better chance for the malicious actor to deceive the victim into performing financial transactions or sharing certain sensitive information. To effectively mitigate this risk, we have identified the below key considerations :
Agent Authentication: In order for the malicious actor to pull off the attack, he/she will need to first impersonate a call center staff from the organisation. Therefore, to allow the customer to have the ability to authenticate the agent easily will be an effective approach to block the attack from being successfully executed.
Journey Standardisation: The customer journey when interacting with genuine staff must be different from fraudulent actors. By including agent authentication as part of the SOP for call center staffs and informing the customers on this SOP will be important to mitigate the risk of social engineering attacks. As the customers get accustomed to the standard journey that involves them carrying out an agent authentication, they will be less likely to fall into the traps of malicious actors even in a stressful situation.
This paper outlines Midships' agent verification solution that is built on TOTP technology. We provide a straightforward and effective solution framework on agent verification that can be implemented on any tech stack. We also offer a readily implementable Ping Identity (ForgeRock) native solution. For any organisation that provide mobile applications to their customers, this solution will grant customers the ability to authenticate an agent from the organisation using their mobile phones.
Midships Solution
Midships’ agent verification solution is built on TOTP technology. When customers onboard to the mobile application on their mobile devices, the device registration journey will include a TOTP seed exchange using secure key exchange protocol. This seed is to be securely stored in both the device and in the backend. This will allows the same OTP to be generated by both the device and the backend that can be used for agent authentication. Our approach allows the realisation of the below desired outcomes:
Bi-Directional Authentication: As TOTP is a symmetric cryptographic algorithm, this allow bi-directional authentication to be possible. An OTP can be generated by the backend and that OTP can be verified by the device. This will allow a user to established the authenticity of the agent.
Wide Coverage: As almost everybody these days owns a smart phone, this approach will be able to cover most, if not all customers. This will allow inclusion of the agent authentication into SOPs to have little concerns over customer coverage.
Offline Support: For the device to generate and verify TOTP, it does not require any internet connectivity. This will allow customers that has limited internet access on their mobile devices to be able to carryout agent authentication in offline manner.
This paper outlines Midships' agent verification solution that is built on TOTP technology. We provide a straightforward and effective solution framework on agent verification that can be implemented on any tech stack. We also offer a readily implementable Ping Identity (ForgeRock) native solution. For any organisation that provide mobile applications to their customers, this solution will grant customers the ability to authenticate an agent from the organisation using their mobile phones.
How it works
AM Authentication Tree Changes
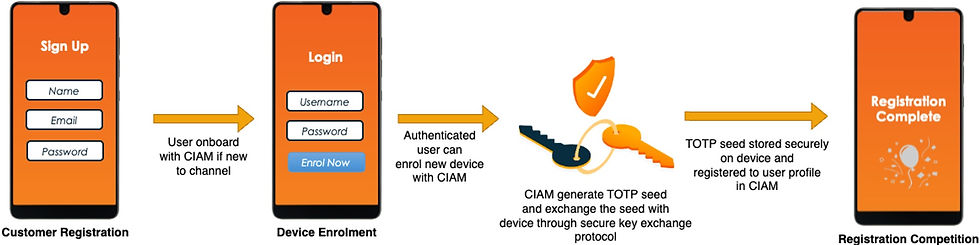
To enable agent verification ability on the mobile device, the device must first be registered with the Customer Identity & Access Management (CIAM) system. During the device enrolment process, the CIAM system will generate a TOTP seed for agent verification, which will be registered to the user profile and also returned to the mobile app via secure key exchange protocol. The mobile app will store the TOTP seed in the device’s secure enclave and can configure access policy to necessitate local authentication using OS-level authenticator options, such as face ID or device pin to further protect the TOTP seed.
Agent Verification
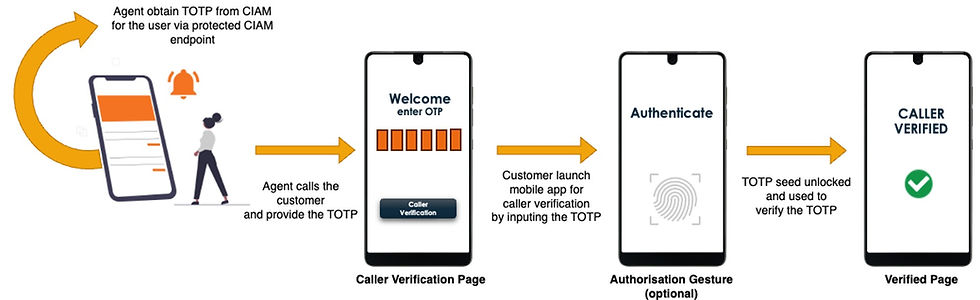
The agent verification process begins with the agent retrieving an TOTP from the CIAM system. The CIAM system will protect the agent verification TOTP generation endpoint such that only authenticated and authorised agent can access this endpoint. The agent will need to provide the CIAM system with the user identifier which the CIAM system will use to pinpoint the seed for TOTP generation. Upon receiving the TOTP, the agent can call the customer and provide the TOTP. The customer can verify this TOTP locally on the device as the device can generate the same TOTP using the same seed stored.
Other Considerations
Seed Dedication And TOTP Time Step
The TOTP seed for agent verification must be dedicated such that the TOTP generated can only be used for agent verification and nothing else. This is particularly important for organisations that already provide TOTP features for user authentication. The seed used for user authentication should never be the same seed used for agent verification. This will ensure the exposure of TOTP to the agent does not amount to opportunities of internal hacking.
The expiry of an TOTP depends on the time step used in TOTP generation. As agent interacts with the customer in real-time, the time step used for agent verification should be in the range of a few minutes to minimise the time window of the TOTP replayability. In addition, to handle time out of sync cases, the CIAM system will need to provide a time sync API for the mobile app to periodically carryout time synchronisation.
Other Communication Medium
This solution can also be applied to email and SMS where the message includes a TOTP for the customer to verify the authenticity of the message. As email and SMS do not involve real time interaction with the user, the time step used for TOTP generation will need to be extended from minutes to hours. The message should also inform the user when the OTP will be expired and provide a customer journey where the customer can request for the message to be resent with a new TOTP.
Are you interested?
If you would like to learn more, please contact sales@midships.io




Comments